Using Cryptographic Algorithms to Create a Temporary Pass Using QR Code Generation Technology
https://doi.org/10.31854/1813-324X-2025-11-3-119-128
EDN: UMCIKU
Abstract
In modern conditions, the security of higher education institutions requires an integrated approach, including both physical protection and cybersecurity. With the growing number of students, faculty, and visitors, as well as increasing threats such as terrorism, vandalism, and cyberattacks, the implementation of effective access control systems is becoming an urgent task. One of the promising solutions is a system for monitoring temporary passes based on QR codes, which ensures not only the restriction of unauthorized access, but also the collection of data on the movement of persons on the territory of the educational institution. The purpose of this study is to develop a methodology for using QR codes in access control systems of higher education institutions using modern cryptographic algorithms, including symmetric encryption (AES-256), asymmetric elliptic curve cryptography (ECC).
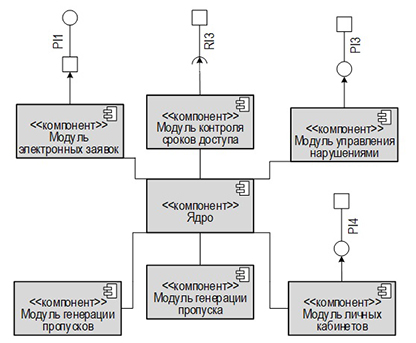
The essence of the proposed solution is an automated system that includes: electronic applications for admission; automatic; QR code generation.codes with encrypted data; control of the validity period of passes; monitoring violations and integration with the Telegram bot for the convenience of users. The principle of the described technique is based on the encryption of the metadata of the pass, followed by the generation of a QR code that can be read and verified by the security service. AES-256 and ECC algorithms are used to ensure a high degree of protection.
The scientific novelty of the solution lies in the combined use of QR codes and modern cryptographic methods, which ensures a high level of security and ease of use in a university setting.
The theoretical significance of the work consists in developing a model of an access control system adapted for educational institutions, taking into account modern threats and requirements of regulatory documents (for example, Decree of the President of the Russian Federation No. 166 dated 30.03.2022).
The practical significance is confirmed by the possibility of direct implementation of the system in educational institutions. The solution allows not only to increase the level of security, but also to optimize administrative processes by automating the issuance of passes and integrating with the Telegram messenger.
About the Authors
Yu. Yu. KalininaRussian Federation
Yu. A. Smirnova
Russian Federation
References
1. GOST R 53704-2009. Complex and integrated security systems. General technical requirements. Moscow: Standartinform 2010. (in Russ.)
2. Timofeeva O.A., Zaitsev A.N., Smurygin A.V. Comprehensive security of an educational institution as a technology of in-tegrated learning. Proceedings of the Vth International Scientific and Practical Conference on Physical culture and health of modern youth, 15 September, 2022, Voronezh, Russian Federation. Voronezh: Voronezh State Pedagogical University Publ.; 2022. p.216‒220. (in Russ.) EDN:DTHCAC
3. GOST R ISO/IEC 17799-2005. Information technology. Code of practice for information security management. Moscow: Standartinform Publ.; 2006. (in Russ.)
4. GOST 34.003-90. Information technology. Set of standards for automated systems. Automated systems. Terms and definitions. Moscow: Izdatelstvo standartov Publ.; 1990. (in Russ.)
5. Kartamyshev A.V., Marenchuk Yu.A., Rozhkov S.Y., Zhuk E.A. Ensuring the integrated security of an educational institution. Proceedings of the IX (66th) Annual Scientific and Practical Conference of the North Caucasus Federal University on Actual Problems of Engineering Sciences, 04‒29 April 2022, Stavropol, Russian Federation. Stavropol: North Caucasus Federal University Publ.; 2022. p.277‒281. (in Russ.) EDN QPBQSJ
6. Zagrebina E.I. To integrated safety educational organizations. Kazan Pedagogical Journal. 2015;1(108):97‒103. (in Russ.) EDN:RXWADS
7. Kalinina Yu.Y. Development of an information system for automating the process of creating a temporary pass to the territory of the Astrakhan State University named after V.N. Tatishchev. Proceedings of the VIIth All-Russian Scientific and Practical Conference on Problems of Increasing the Efficiency of Scientific Work in the Russian Military-Industrial Complex, 11‒12 April 2024, Znamensk, Russian Federation. Astrakhan: Astrakhan State University named after V.N. Tatishchev Publ.; 2024. p.91‒94. (in Russ.) EDN:BQZIRB
8. QR-Code-Generator. QR Codes 101: A Beginner’s Guide. URL: https://ru.qr-code-generator.com/qr-code-marketing/qr-codes-basics [Accessed 04 June 2025]
9. GOST R ISO/IEC 18004-2015. Information technology. Automatic identification. Bar coding. Encyclopedia of QR code symbols. Moscow: Stratinform; 2016. (in Russ.)
10. ISO/IEC 18004:2015. Information technology. Methods of automatic identification and data collection. Specification of QR codes and barcodes. Geneva: ISO; 2015.
11. Serebryakova S.G. Can QR-Code Become the Future of Digital Storytelling? Proceedings of the XXIIIth International Baltic Communication Forum «Bulletin of the Faculty of Social Digital Technologies», 03‒04 December 2021, St. Petersburg, Russian Federation. St. Petersburg: The Bonch-Bruevich Saint Petersburg State University of Telecommunications Publ.; 2021. p.295‒298. (in Russ.) EDN:PHWWDE
12. Zadorozhny A.V. The use of a QR code in the process of monitoring class attendance. Proceedings of the XIth International Youth Forum "Education. Science. Production", 01‒20 October 2019, Belgorod, Russian Federation. Belgorod: Belgorod State Technological University named after V.G. Shukhov Publ.; 2019. p.2928‒2932. (in Russ.) EDN:THNKCB
13. Kalinina Yu.Y., Smirnova Yu.A. Automation of the access control process at the university using a Telegram bot. Proceedings of the Vth International Scientific and Practical Conference on Current Trends in the Development of Information Technologies in Scientific Research and Applied Fields, 25‒26 April 2024, Vladikavkaz, Russian Federation. Vladikavkaz: North Caucasus Mining and Metallurgical Institute Publ.; 2024. p.52‒55. (in Russ.) EDN:GBZBYA
14. Semenov S.N., Sai S.V. Features of the AES: Rijndael encryption algorithm. Proceedings of the Regional Scientific and Practical Conference «TOGU-Start: Fundamental and Applied Research of Young People», 12‒16 April 2021, Khabarovsk, Russian Federation. Khabarovsk: Pacific State University Publ.; 2021. p.345‒350. (in Russ.) EDN:AMLWHM
15. Volokitina T.S. Software implementation of block encryption with variable keys based on the AES 256 cipher. Proceedings of the Xth International Research Competition on Basic and Applied scientific Research, 05 December 2022, Ufa, Russian Federation. Ufa: Nauchno-izdatelskii tsentr Vestnik nauki Publ.; 2022. p.67‒78. (in Russ.) EDN:TMAWEA
16. Vorobyov A.P., Krotova E.L., Vorobyova E.Y. Advantages of cryptography on elliptic curves for solving authentication problems. Bulletin of the Ural Federal District. Security in the Information Sphere. 2024;2(52):99‒105. (in Russ.) DOI:10.14529/secur240210. EDN:GZNHGR
17. Olshansky V.K. Elliptic curves in modern cryptography. Proceedings of the XVIIth St. Petersburg International Conference «Regional Informatics (RI-2020)», 28‒30 October 2020, St. Petersburg, Russian Federation, vol.1. St. Petersburg: St. Petersburg Society of Informatics, Computer Technology, Communication and Control Systems Publ.; 2020. p.351‒352. (in Russ.) EDN:BJESRU
18. Kalinina Yu.Y., Smirnova Yu.A., Demina R.Yu. A method and algorithm of intelligent decision-making support system for generation of temporary access passes to the territory of higher educational institutions. Bulletin of Tambov State Technical University. 2025;31(1):70‒80. (in Russ.) DOI:10.17277/vestnik.2025.01.pp.070-080. EDN:NPFYUL
Review
For citations:
Kalinina Yu.Yu., Smirnova Yu.A. Using Cryptographic Algorithms to Create a Temporary Pass Using QR Code Generation Technology. Proceedings of Telecommunication Universities. 2025;11(3):119-128. (In Russ.) https://doi.org/10.31854/1813-324X-2025-11-3-119-128. EDN: UMCIKU


































