Corporate Algorithm of Multiple Access in Cyberspace
https://doi.org/10.31854/1813-324X-2025-11-3-97-107
EDN: GUNCQI
Abstract
Relevance. An integral component of cyberspace are access systems that ensure the distribution of cyberspace information and communication resources among users. The development and implementation of digital technologies requires making adjustments to the architecture and principles of functioning of access systems. At the same time, it should be borne in mind that the requirements imposed on them can be diverse, contradictory and determined by the specifics of the subject area. The purpose of the research is to propose a competitive algorithm for multiple access, the main idea of which is the rejection of the principle of adversarial load sources. The “corporativeness" of the algorithm is manifested in the use of the principle of “fair distribution” of a common resource, the transmission channel, so that all data from all sources of the load is collected and transmitted corporately without delay/loss. The main requirement for the functioning of a corporate multiple access system is to meet the general criterion of optimality. Such criteria can be: the weighted average proportion of data blocks received correctly and on time, or the weighted average delay time in transmitting data blocks, or the weighted average proportion of lost data blocks.
Methods. The article outlines the concept of a corporate multiple access algorithm based on a combined method for dividing a common transmission channel: temporary separation is used between groups of load sources, and random synchronous access is used within each group. To implement the corporate access principle, a dynamic access control procedure is used.
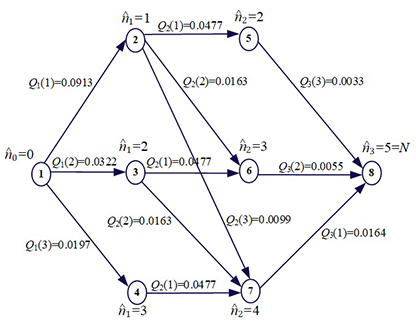
Results. A mathematical model of a corporate multiple access network and expressions for calculating the probabilistic-temporal characteristics of data block transmission have been developed. The optimization problem is formulated: choosing the optimal mode of operation of the access network, which provides for such a distribution of time windows between load sources that the extremum of the general optimality criterion is achieved. A three–stage algorithm for solving the optimization problem is proposed: stage 1 is the calculation of all possible values of the selected optimization criterion, for which the weighted average proportion of data blocks received correctly and on time is taken, stage 2 is the construction of a graphical model of the optimization problem, and stage 3 is the finding of the shortest path for the constructed graph, the set of edges that make up such a path will be solving the problem. The approbation of this algorithm is presented.
The theoretical significance is the expansion in the formalization of the description of the architecture of cyberspace, the development of methods, technologies and mathematical models of multiple access in cyberspace, as well as in the calculated expressions obtained, algorithms for optimizing the functioning of systems that implement a corporate approach to multiple access.
About the Authors
N. A. VerzunRussian Federation
M. O. Kolbanev
Russian Federation
B. Ya. Sovetov
Russian Federation
References
1. Analytical report. Cybersecurity strategies. (in Russ.) URL: https://www.infowatch.ru/sites/default/files/publication_
2. file/analiticheskiy-otchet-strategii-kiberbezopasnosti.pdf. [Accessed 18.06.2025]
3. ISO/IEC 27032:2023. Cybersecurity ‒ Guidelines for Internet security. 2023. URL: https://www.iso.org/standard/76070.html [Accessed 18.06.2025]
4. Digital 2024: Global Overview Report // Kepios. 2024. URL: https://datareportal.com/reports/digital-2024-global-overview-report (Accessed 18.06.2025)
5. Verzun N.A., Kolbanev M.O. Chapter 5. Models of access hazards in cyberspace. In: Models of digital danger in cybernetic and cognitive spaces. St. Petersburg: St. Petersburg State University of Economics Publ.; 2023. p.93‒123. (in Russ.) EDN:AAHVOZ
6. Vaezi M., Ding Z., Poor H.V. Multiple Access Techniques for 5G Wireless Networks and Beyond. Cham: Springer; 2019. DOI:10.1007/978-3-319-92090-0
7. Bakulin M.G., Ben Rejeb T.B.K., Kreindelin V.B., Mironov Yu.B., Pankratov D.Yu., Smirnov A.E. Multiple Access Schemes for 5G And Next Generations Communication Systems. Electrosvyaz. 2022;5:16‒21. (in Russ.) DOI:10.34832/ELSV.2022.30.5.002. EDN:KCCLIL
8. Basharat M., Ejaz W., Naeem M., Khattak A.M., Anpalagan A. A survey and taxonomy on nonorthogonal multiple-access schemes for 5G networks. Transactions on Emerging Telecommunications Technologies. 2018;29(1):e3202. DOI:10.1002/ett.3202
9. Roslyakov A.V. Fifth–Generation Fixed-Line Networks. Moscow: Kolos-S Publ.; 2024. 232 p. (in Russ.) EDN:DXGSFN
10. Bogatyrev V.A., Bogatyrev S.V., Bogatyrev A.V. Assessment of the readiness of a computer system for timely servicing of requests when combined with information recovery of memory after failures. Scientific and Technical Journal of Information Technologies, Mechanics and Optics. 2023;23(3):608–617 (in Russ.) DOI: 10.17586/2226-1494-2023-23-3-608-617. EDN:JWPOKM
11. Koucheryavy A., Paramonov A., Makolkina A., Muthanna A. S. A., Vybornova A., Dunaytsev R., et al. 3 Dimension Multilayer Heterogenous Ultra Dense Networks. Telecom IT. 2022;10(3):1–12. (in Russ.) DOI:10.31854/2307-1303-2022-10-3-1-12. EDN:LHLYEM
12. Zakharov M.V., Kirichek R.V. Methods of building a super-dense e-health network using edge computing. Proceedings of the 75th Scientific and Technical Conference of the St. Petersburg NTO RES named after A.S. Popov, dedicated to Radio Day. Saint-Petersburg: SPbSETU "LETI" Publ.; 2020. p.145–147. (in Russ.) EDN:XVIGBJ
13. Roslyakov A.V., Gerasimov A.V. Deterministic Networks and Their Standardization. Standards and Quality. 2024;7:42-47. (in Russ.) DOI:10.35400/0038-9692-2024-7-70-24. EDN:UTBDXB
14. Verzun N., Kolbanev M., Shamin A. The Architecture of the Access Protocols of the Global Infocommunication Resources. Computers. 2020;9(2):49. DOI:10.3390/computers9020049. EDN:KJCHRF
15. Verzun N., Kolbanev M., Vorobeva D. Access Control Model to Global Infocommunication Resources. Proceedings of the Majorov International Conference on Software Engineering and Computer Systems, 12–13 December 2019, Saint Petersburg, Russian Federation, vol.11. Saint Petersburg: Federal State Autonomous Educational Institution of Higher Education “National Research University ITMO” Publ.; 2020. p.218‒221. EDN:RDFFNM
16. Marakulin V.M. Elements of the theory of cooperative games. (in Russ.) URL: http://old.math.nsc.ru/~mathecon/Marakulin/CooGAMES.pdf [Accessed 18.06.2025]
17. Gezalov E.B. Model of heterogeneous local communication network with synchronous time access protocol, considering the reliability of its elements. T-Comm. 2021;15(3):25‒29. (in Russ.) DOI:10.36724/2072-8735-2021-15-2-25-29. EDN:WDTOSM
18. Verzun N.A., Vorobyov A.I., Poimanova E.D. Modeling information transfer process in network with access rights differentiation. Journal of Instrument Engineering. 2014;57(9):33‒37. (in Russ.) EDN:SMPASB
19. Vishnevsky V.M. Theoretical foundations of computer network design. Moscow: Technosphere Publ.; 2003. p. 512. (in Russ.)
20. Wentzel E.S. Investigation of surgery. Tasks, principles, methodology. Moscow: Nauka Publ.; 1988. 208 p. (in Russ.)
21. Bellman R., Dreyfus S. Applied Dynamic Programming. Princeton: University Press; 1962. DOI:10.1515/9781400874651
22. Rachkov M.Y. Optimal control in technical systems. Moscow: Yurait Publ.; 2023. 120 p. (in Russ.)
Review
For citations:
Verzun N.A., Kolbanev M.O., Sovetov B.Ya. Corporate Algorithm of Multiple Access in Cyberspace. Proceedings of Telecommunication Universities. 2025;11(3):97-107. (In Russ.) https://doi.org/10.31854/1813-324X-2025-11-3-97-107. EDN: GUNCQI


































