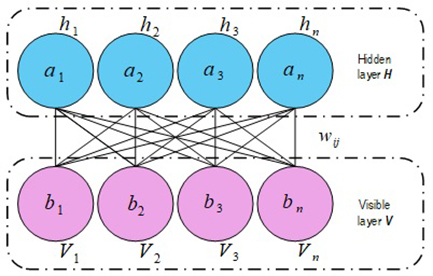
Comprehensive Review of Deep Learning in Intrusion Detection Systems
https://doi.org/10.31854/1813-324X-2025-11-3-72-86
EDN: HSXTLS
Abstract
Deep learning methods play a crucial role in enhancing the effectiveness of intrusion detection systems. This study presents a comparative analysis of seven deep learning models, including autoencoders, restricted Boltzmann machines, deep belief networks, convolutional and recurrent neural networks, generative adversarial networks, and deep neural networks. The primary focus is on accuracy, precision, and recall metrics, evaluated using the NSL-KDD dataset. The analysis demonstrated the high effectiveness of recurrent neural networks, which achieved an accuracy of 99.79 %, precision of 99.67 %, and recall of 99.86 %.
The objective of the study: of this paper is to enhance the effectiveness of intrusion detection systems through a comparative analysis of the performance of various deep learning models and an assessment of their applicability in the context of dynamic network security threats.
The proposed solution involves a comparative analysis of seven deep learning models to identify the most effective ones for network security tasks. This analysis aids in selecting the optimal models for specific security requirements.
The evaluation methodology involves the use of the benchmark dataset NSL-KDD, which contains various types of attacks and normal connections. The key evaluation metrics are accuracy, precision, and recall.
The system implementation is based on deep learning frameworks such as TensorFlow. The results of the system’s performance and their interpretation are presented in the paper.
Experiments with the NSL-KDD dataset demonstrated accuracy, precision, and recall for all the deep learning models considered.
The scientific novelty is the ability to obtain formal performance evaluations of various deep learning models for intrusion detection systems, taking into account their architectural features, the processing of temporal and spatial data, as well as the characteristics of network traffic and attack types.
The theoretical significance is the expansion of methods for evaluating the effectiveness of intrusion detection systems through the analysis and comparison of the performance of deep learning models in the context of processing complex and high-dimensional network data.
The practical significance is the application of the comparative analysis results for selecting the most effective solutions in intrusion detection systems and optimizing them for real-world operating conditions.
About the Authors
M.M.A. Al-TameemiRussian Federation
A.A.H. Alzaghir
Russian Federation
M.A.M. Alsweity
Russian Federation
References
1. Navya V.K., Adithi J., Rudrawal D., Tailor H., James N. Intrusion Detection System Using Deep Neural Networks (DNN). Proceedings of the International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation, ICAECA, 08‒09 October 2021, Coimbatore, India. IEEE; 2022. DOI:10.1109/ICAECA52838.2021.9675513
2. Vinayakumar R., Soman K.P. Poornachandran P. Applying convolutional neural network for network intrusion detection. Proceedings of the International Conference on Advances in Computing, Communications and Informatics, ICACCI, 13‒16 September 2017, Udupi, India. IEEE; 2017. p.1222‒1228. DOI:10.1109/ICACCI.2017.8126009
3. Wu Y., Lee W.W., Xu Z., Ni M. Large-scale and robust intrusion detection model combining improved deep belief network with feature-weighted SVM. IEEE Access. 2020;8:98600‒98611. DOI:10.1109/ACCESS.2020.2994947. EDN:APJZGY
4. Alpaydin E. Introduction to Machine Learning. MIT Press; 2020.
5. Aldwairi T., Perera D., Novotny M.A. An evaluation of the performance of Restricted Boltzmann Machines as a model for anomaly network intrusion detection. Computer Networks. 2018;144:111‒119. DOI:10.1016/j.comnet.2018.07.025
6. Choi H., Kim M., Lee G., Kim W. Unsupervised learning approach for network intrusion detection system using autoencoders. The Journal of Supercomputing. 2019;75(9):5597‒5621. DOI:10.1007/s11227-019-02805-w. EDN:RJBUQU
7. Shahriar M.H., Haque N.I., Rahman M.A., Alonso M. G-ids: Generative adversarial networks assisted intrusion detection system. Proceedings of the 44th Annual Computers, Software, and Applications Conference, COMPSAC, 13–17 July 2020, Virtual, Madrid. IEEE; 2020. p.376‒385. DOI:10.1109/COMPSAC48688.2020.0-218. EDN:DJVEFI
8. Al-Qatf M., Lasheng Y., Al-Habib M., Al-Sabahi K. Deep Learning Approach Combining Sparse Autoencoder With SVM for Network Intrusion Detection. IEEE Access. 2018;6:52843‒52856. DOI:10.1109/ACCESS.2018.2869577
9. Shone N., Ngoc T.N., Phai V.D., Shi Q. A Deep Learning Approach to Network Intrusion Detection. IEEE Transactions on Emerging Topics in Computational Intelligence. 2018;2(1):41‒50. DOI:10.1109/TETCI.2017.2772792
10. Li Z., Qin Z., Huang K., Yang X., Ye S. Intrusion Detection Using Convolutional Neural Networks for Representation Learning. Proceedings of the 24th International Conference on Neural Information Processing, ICONIP, 14–18 November 2017, Guangzhou, China. Lecture Notes in Computer Science, vol.10638. Cham: Springer; 2017. p.858‒866. DOI:10.1007/978-3-319-70139-4_87
11. Wang S., Wang J., Lu H., Zhao W. A novel combined model for wind speed prediction–Combination of linear model, shallow neural networks, and deep learning approaches. Energy. 2021;234:121275. DOI:10.1016/j.energy.2021.121275. EDN:FAJRCK
12. Javaid A., Niyaz Q., Sun W., Alam M. A Deep Learning Approach for Network Intrusion Detection System. Proceedings of the 9th EAI International Conference on Bio-inspired Information and Communications Technologies, formerly BIONETICS, 3‒5 December 2015, New York, USA. 2016. p.21‒26. DOI:10.4108/eai.3-12-2015.2262516
13. Manimaran A., Chandramohan D., Shrinivas S.G., Arulkumar N. A comprehensive novel model for network speech anomaly detection system using deep learning approach. International Journal of Speech Technology. 2020;23(2):305‒313. DOI:10.1007/s10772-020-09693-z. EDN:URAWUT
14. Alrayes F.S., Zakariah M., Amin S.U., Khan Z.I., Helal M. Intrusion Detection in IoT Systems Using Denoising Autoencoder. IEEE Access. 2024;12:122401‒122425. DOI:10.1109/ACCESS.2024.3451726. EDN:VCPDLT
15. Vincent P., Larochelle H., Bengio Y., Manzagol P.A. Extracting and composing robust features with denoising autoencoders. Proceedings of the 25th International Conference on Machine Learning, 5‒9 July 2008, Helsinki, Finland. Association for Computing Machinery; 2008. p.1096‒1103. DOI:10.1145/1390156.1390294
16. Vincent P., Larochelle H., Lajoie I., Bengio Y., Manzagol P.A., Bottou L. Stacked Denoising Autoencoders: Learning Useful Representations in a Deep Network with a Local Denoising Criterion. Journal of Machine Learning Research. 2010;11:3371‒3408. EDN:OCLKDJ
17. Zhang N., Ding S., Zhang J., Xue Y. An overview on restricted Boltzmann machines. Neurocomputing. 2018;275:1186‒1199. DOI:10.1016/j.neucom.2017.09.065
18. Mayuranathan M., Murugan M., Dhanakoti V. Retracted article: best features based intrusion detection system by RBM model for detecting DDoS in cloud environment. Journal of Ambient Intelligence and Humanized Computing. 2021;12(3):3609‒3619. DOI:10.1007/s12652-019-01611-9. EDN:LAAOLK
19. Seo S., Park S., Kim J. Improvement of Network Intrusion Detection Accuracy by Using Restricted Boltzmann Machine. Proceedings of the 8th International Conference on Computational Intelligence and Communication Networks, CICN, 23‒25 December 2016, Tehri, India. IEEE; 2016. p.413‒417. DOI:10.1109/CICN.2016.87
20. Balakrishnan N., Rajendran A., Pelusi D., Ponnusamy V. Deep Belief Network Enhanced Intrusion Detection System to Prevent Security Breach in the Internet of Things. Internet of Things. 2021;14:100112. DOI:10.1016/j.iot.2019.100112. EDN:CZRBGW
21. Yang Y., Zheng K., Wu C., Niu X., Yang Y. Building an Effective Intrusion Detection System Using the Modified Density Peak Clustering Algorithm and Deep Belief Networks. Applied Sciences. 2019. Vol. 9. Iss. 2. P. 238. DOI:10.3390/app9020238. EDN:ABGPER
22. Parhizkari S. Anomaly Detection in Intrusion Detection Systems. 2023. DOI:10.5772/intechopen.112733
23. Mehibs S.M., Hashim S.H. Proposed Network Intrusion Detection System in Cloud Environment Based on Back Propagation Neural Network. Journal of University of Babylon for Pure and Applied Sciences. 2018;26(1):29‒40. DOI:10.29196/jub. v26i1.351
24. Al-Tameemi M.M.A., Alzaghir A.A.H. Improving Network Security Through Deep Learning RNN Approach. Computational Nanotechnology. 2024;11(4):114–121. DOI:10.33693/2313-223X-2024-11-4-114-121. EDN:GPCZUD
25. Smagulova K., James A.P. A survey on LSTM memristive neural network architectures and applications. The European Physical Journal Special Topics. 2019;228(10):2313‒2324. DOI:10.1140/epjst/e2019-900046-x. EDN:HRKIKB
26. Han K., Yu D., Tashev I. Speech emotion recognition using deep neural network and extreme learning machine. Interspeech 2014. DOI:10.21437/Interspeech.2014-57
27. Roy S.S., Mallik A., Gulati R., Obaidat M.S., Krishna P.V. A deep learning based artificial neural network approach for intrusion detection. Proceedings of the Third International Conference on Mathematics and Computing, ICMC 2017, 17‒21 Janu-ary 2017, Haldia, India. Communications in Computer and Information Science, vol.655. Singapore: Springer; 2017. p.44‒53. DOI:10.1007/978-981-10-4642-1_5
28. Gowdhaman V., Dhanapal R. An intrusion detection system for wireless sensor networks using deep neural network. Soft Computing. 2022;26(23):13059‒13067. DOI:10.1007/s00500-021-06473-y. EDN:KHFOPY
29. Yang Y., Zheng K., Wu C., Niu X., Yang Y. Building an Effective Intrusion Detection System Using the Modified Density Peak Clustering Algorithm and Deep Belief Networks. Applied Sciences. 2019:9(2):238. DOI:10.3390/app9020238. EDN:ABGPER
30. Mohammadpour L., Ling T.Ch., Liew Ch.S., Aryanfar A. A Survey of CNN-Based Network Intrusion Detection. Applied Sciences. 2022;12(16):8162. DOI:10.3390/app12168162. EDN:EFJJTR
31. Razavian A.S., Azizpour H., Sullivan J., Carlsson S. CNN features off-the-Shelf: An Astounding Baseline for Recognition. arXiv. 2014. DOI:10.48550/arXiv.1403.6382
32. Jo W., Kim S., Lee C., Shon T. Packet preprocessing in CNN-based network intrusion detection system. Electronics. 2020;9(7):1151. DOI:10.3390/electronics9071151. EDN:XVUGFM
33. Sabuhi M., Zhou M., Bezemer C.P., Musilek P. Applications of Generative Adversarial Networks in Anomaly Detection: A Systematic Literature Review. IEEE Access. 2021;9:161003‒161029. DOI:10.1109/ACCESS.2021.3131949. EDN:TJDTSD
34. Dunmore A., Jang-Jaccard J., Sabrina F., Kwak J. A Comprehensive Survey of Generative Adversarial Networks (GANs) in Cybersecurity Intrusion Detection. IEEE Access. 2023;11:76071‒76094. DOI:10.1109/ACCESS.2023.3296707. EDN:NOKCVG
Review
For citations:
Al-Tameemi M., Alzaghir A., Alsweity M. Comprehensive Review of Deep Learning in Intrusion Detection Systems. Proceedings of Telecommunication Universities. 2025;11(3):72-86. https://doi.org/10.31854/1813-324X-2025-11-3-72-86. EDN: HSXTLS


































