Communication Infrastructure Modeling Based on Simulation and Semi-Natural Modeling
https://doi.org/10.31854/1813-324X-2025-11-1-70-83
EDN: QOBBRA
Abstract
The relevance of the research is explained by the existing contradiction of the subject area, which consists in the communication infrastructure of the critical information infrastructure (CII) object dynamically changing in the process of functioning, as well as the methods of the intruder's impact on the CII object, as well as the methods of the intruder's impact on the CII object, which create preconditions for reducing the level of information security and the capabilities of the existing methods of assessing the object's security based on signatures, expert approach, as well as methods and means of ensuring information security, which do not allow taking into account such dynamics of changes in the level of information security of the object.
Purpose of the research. Provision of information security of communication infrastructure of CII objects by taking into account communication and configuration parameters, dynamics of interacting subjects.
Research methods. Mathematical methods of systems theory and system analysis of probability theory, methods of graph theory, methods of simulation modeling.
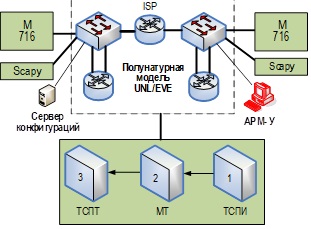
Results. The article presents a method of modeling of communication infrastructure that allows to form parametric accurate simulation models of the CII object to study the properties of security and stability, to simulate the impact of an intruder on the CII object.
Novelty. A method of modeling the communication infrastructure based on configuration and communication parameters of the CII object has been developed, taking into account the dynamics of communication infrastructure interaction, its information security policy and intruder actions.
Theoretical significance. Development of information security methods in the field of modeling the communication infrastructure of CII objects on the basis of hypergraphs, nested colored Petri nets, allowing to take into account the dynamics of interacting subjects (communication and configuration infrastructure, information security policy, the impact of the intruder).
Practical significance. The modeling method allows to take into account configuration and communication peculiarities of construction and functioning of the CII object, parameters of the intruder's impact on the CII object, the existing security policy, to model the stability property, to conduct research of the influence of interacting subjects on the security of the CII object, to reduce the dependence on expert assessments, to receive parametrically justified assessments of the security of the communication infrastructure of the CII object.
References
1. Zapechnikov S.V., Miloslavskaya N.G., Tolstoj A.I. Basics of Building Virtual Private Networks. Moscow: Goryachaya liniya ‒ Telekom Publ.; 2011. 249 p. (in Russ.)
2. Zahvatov M.A. Building Virtual Private Networks Based on MPLS Technology. Moscow: Cisco Systems Publ.; 2001. (in Russ.)
3. Zegzhda D.P. Cybersecurity of the Digital Industry. Theory and Practice of Functional Resistance to Cyberattacks. Moscow: Goryachaya liniya – Telekom Publ.; 2023. 500 p. (in Russ.)
4. Petrenko S.A. Cyber Resilience of Digital Industry 4.0. Saint Petersburg: Afina Publ.; 2020. 256 p. (in Russ.)
5. Petrenko S.A. Cyber Resilience Management: Problem Statement. Zaŝita informacii. Inside. 2019;3(87):16–24. (in Russ.) EDN:HHVJNX
6. Shtyrkina A.A. Cyber-Physical Systems Sustainability Based on Graph Theory. Information Security Problems. Computer Systems. 2021;2:145–150. (in Russ.) EDN:HACNAD
7. Bochkov M.V., Vasinev D.A. Modeling the Stability of Critical Information Infrastructure Based on Hierarchical Hypernets and Petri Nets. Voprosy kiberbezopasnosti. 2024;1(59):108‒151. (in Russ.) DOI:10.21681/2311-3456-2024-1-108-115. EDN:KWFIOY
8. Minaev M.V., Bondar K.M., Dunin V.S. Modeling of Cyber Resilience Information Infrastructure of the Internal Affairs Ministry of Russia. Kriminologicheskij zhurnal. 2021;3:123–128. (in Russ.) DOI:10.24412/2687-0185-2021-3-123-128. EDN:EAKMQK
9. Osipenko A.A., Chirushkin K.A., Skorobogatov S.Yu., Zhdanova I.M., Korchevnoj P.P. Simulation of Computer Attacks on Software-Configured Networks Based on Stochastic Networks Transformation. Izvestiya Tula State University. Technical Sciences. 2023;2:274–281. (in Russ.) DOI:10.24412/2071-6168-2023-2-274-281. EDN:VNGXMX
10. Vang L., Egorova L.K., Mokryakov A.V. Development of Hypergraph Theory. Journal of Computer and Systems Sciences International. 2018;57(1):109‒114. DOI:10.1134/S1064230718010136. EDN:XXVAJV
11. Velichko V.V., Popkov V.K. Models and Methods for Increasing the Survivability of Modern Communication Systems. Moscow: Goryachaya liniya – Telekom Publ.; 2017. 270 p. (in Russ.)
12. Popkov G.V., Popkov V.K. Mathematical Foundations of Communication Network Modeling. Moscow: Goryachaya liniya – Telekom Publ.; 2018. 182 p. (in Russ.)
13. Kolosok I.N., Gurina L.A. Assessment of Cyber Resilience Indices of Information Collection and Processing Systems in Electric Power Systems Based on Semi-Markov Models. Voprosy kiberbezopasnosti. 2021;6(46):2‒11. (in Russ.) DOI:10.21681/2311-3456-2021-6-2-11. EDN:IJWNVI
14. Gurina L.A. Increasing Cyber Resilience of SCADA and WAMS in the Event of Cyber Attacks on the Information and Communication Subsystem of the Electric Power System. Voprosy kiberbezopasnosti. 2022;2(48):18‒26. (in Russ.) DOI:10.21681/2311-3456-2022-2-18-26
15. Gurina L.A. Assessment of Cyber Resilience of Operational Dispatch Control System of EPS. Voprosy kiberbezopasnosti. 2022;3(49):23‒31. (in Russ.) DOI:10.21681/2311-3456-2022-3-23-31. EDN:SAPIYH
16. Chirkova N.E. Analysis of Existing Approaches to Assessing the Cyber Resilience of Heterogeneous Systems. Proceedings of the International Scientific and Practical Conference on Technology and Security of Penal System Facilities, 18‒19 May 2022, Voronezh, Russian Federation. Ivanovo: PressTo Publ.; Voronezh Institute of the Federal Penitentiary Service of Russia Publ.; 2022. p.408–410. (in Russ.) EDN:CPZRVP
17. Makarenko S.I. Dynamic Model of Communication System in Conditions the Functional Multilevel Information Conflict of Monitoring and Suppression. Systems of Control, Communication and Security. 2015;3:122–186. (in Russ.) DOI:10.24411/ 2410-9916-2015-10307. EDN:UKSPAV
18. Bobrov V.N., Zaharchenko R.I., Buharov E.O., Kalach A.V. System Analysis and Justification of Selection of Models for Ensuring Cyber-Stable Functioning of Critical Information Infrastructure Facilities. Vestnik of Voronezh Institute of the Russian Federal Penitentiary Service. 2019;4:31–43. (in Russ.) EDN:DPJJCN
19. Levshun D. Hierarchical Model for the Design of Microcontroller-Based Systems Protected from Cyber-Physical Attacks. Proceedings of Telecommunication Universities. 2023;9(1):105‒115. (in Russ.) DOI:10.31854/1813-324X-2023-9-1-105-115. EDN:QCZRIH
20. Kostogryzov A.I., Nistratov A.A., Golosov P.E. Methodological Provisions on Probabilistic Prediction of Information Systems Operation Quality. Part 2. Modeling Using “Black Boxes”. Voprosy kiberbezopasnosti. 2024;6(64):2‒27. (in Russ.) DOI:10.21681/2311-3456-2024-6-2-27. EDN:ELOIDW
21. Yazov Yu.K., Panfilov A.P. Composite Petri-Markov Networks With Special Construction Conditions for Modeling Information Security Threats. Voprosy kiberbezopasnosti. 2024;2(60):53‒65. (in Russ.) DOI:10.21681/2311-3456-2024-2-53-65. EDN:TEJAVM
22. Vodopyanov A.S. Using Digital Twins to Ensuring Information Security of Cyberphysical Systems. Voprosy kiberbezopasnosti. 2024;4(62):140‒144. (in Russ.) DOI:10.21681/2311-3456-2024-4-140-144. EDN:XTJILH
23. Skryl S.V., Iczkova A.A., Ushakov K.E. On the Possibility of Improving the Procedures for Quantifying Information Protection of Critical Information Infrastructure Objects from Threats of Unauthorized Access. IT Security. 2024;31(3):94‒104. (in Russ.) DOI:10.26583/bit.2024.204. EDN:CZFYY
24. Vasinev D.A. Application of Operating Systems with Open Source Code in of Communication Equipment for Networks with Commutation of Packages. Voprosy kiberbezopasnosti. 2016;4(17):36‒44. (in Russ.) DOI:10.21681/2311-3456-2016-4-36-44. EDN:XCMVAV
25. Vasinev D., Solovev M. Proposals for Universal Protocol Fuzzer Construction. Proceedings of Telecommunication Universities. 2023;9(6):59–67. (in Russ.) DOI:10.31854/1813-324X-2023-9-6-59-67. EDN:AABMEE
26. Vasinev D.A., Bochkov M.V., Kirianov A.V., Andreev S.Iu., Polekhin A.A., Senotrusov I.A., et al. Method and Software and Hardware System for Assessing Security of Telecommunication and Terminal Equipment of Critical Information Infrastructure. Patent RF, no. 2831928 C1, 16.12.2024. (in Russ.)
Review
For citations:
Vasinev D.A. Communication Infrastructure Modeling Based on Simulation and Semi-Natural Modeling. Proceedings of Telecommunication Universities. 2025;11(1):70-83. (In Russ.) https://doi.org/10.31854/1813-324X-2025-11-1-70-83. EDN: QOBBRA

































