Ensuring Information Security of Information Systems to be Integrated Based on Trust
https://doi.org/10.31854/1813-324X-2024-10-4-110-125
EDN: MZMYXF
Abstract
Relevance. Information systems are integrated with each other, which leads to the need to ensure the protection of the integrated system. The level of trust requires formalizing the concept of trust and studying its nature and structure.
The purpose of the article is to remove the contradiction between the needs to provide access to the resources of the resulting integrated system and ensure compliance with the information security requirements of each of the integrated systems by formulating the concept of trust from the information security perspective.
Methods used: systems analysis, risk management theory, resolutions, iSoft operator equation synthesis method.
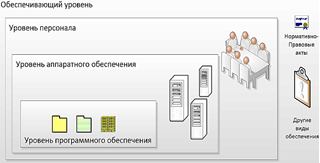
Results. Main shortcomings of existing approaches to the formalization of the concept of “trust” are identified. Based on the FIST information system model, a functional trust structure has been developed and formalized in IDEF0 notation for all levels of integrated information systems: supporting level, personnel level, hardware and software levels. Examples of violation of trust and examples of tools for creating trust for each level of the information system are given. The adequacy of the model is illustrated by the example of real integration of information systems. Application of the proposed trust model made it possible to identify features that increase information security risks for the integrated information system from the example.
Novelty. An interpretation of trust as a measure of information security is proposed, in contrast to “risk” as a measure of danger. A tool for quantitative assessment of trust is proposed. A necessary and sufficient condition for creating maximum trust in an information system is formulated and proven by the resolution method
Practical significance. The proposed trust model can be used in the development of guidance documents regulating the process of integration of information systems, in setting requirements for service personnel and creating training programs for them, for developing information security tools and methods for their application.
About the Authors
V. V. GryzunovRussian Federation
A. S. Krjukov
Russian Federation
A. V. Shestakov
Russian Federation
I. A. Zikratov
Russian Federation
References
1. Chernykh A. The main directions of federal state information systems and classified data. Legal Informatics. 2018;2:47‒56. (in Russ.) EDN:XRPRMT
2. Yan Z., Holtmanns S. Trust Modeling and Management: From Social Trust to Digital Trust. Computer Security, Privacy and Politics: current Issues, Challenges and Solutions. 2008:290‒323. DOI:10.4018/978-1-59904-804-8.ch013
3. Chahal R.K., Kumar N., Batra S. Trust management in social Internet of Things: A taxonomy, open issues, and challenges. Computer Communications. 2020;150:13‒46. DOI:10.1016/j.comcom.2019.10.034
4. Burlov V.G., Gryzunov V.V. Evaluation of the effectiveness of geographic information systems adaptation to destabilizing factors. Journal of Physics: Conference Series. 2020;1703:012016. DOI:10.1088/1742-6596/1703/1/012016
5. Selifanov V.V., Gordeev A.S., Karmanov I.N. Requirements for information sequrity in cross-network interaction of the state information systems with other information systems. Interexpo GEO-Sibiria. 2018;7:277‒282. (in Russ.) EDN:YORFLV
6. Prokushev Ya.E., Ponomarenko S.V., Ponomarenko S.A. The Modeling of information security system design processes in state information systems. Computational Nanotechnology. 2021;1:26‒37. (in Russ.) DOI:10.33693/2313-223X-2021-8-1-26-37. EDN:XJMNND
7. Gryzunov V.V Kornienko A.A., Glukharev M.L., Kryukov A.S. Selection of trust models when integrating distributed information systems of critical application. Information Security Problems. Computer Systems. 2021;479‒90. (in Russ.) DOI:10.48612/jisp/ev3e-fmtu-x25h. EDN:VMALWC
8. Kruglikov S., Dmitriev V., Stepanian A., Maksimovich E. Information security of information systems with elements of centralization and decentralization. Voprosy kiberbezopasnosti. 2022;1(35):2‒7. (in Russ.) DOI:10.21681/2311-3456-2020-01-02-07. EDN:HVFMFK
9. Shiverov P.K., Bondarenko V.V. The concept of trust in the context of information security. Proceedings of the International Conference and Youth School on Information Technologies and Nanotechnologies, ITNT-2016, 17‒19 May 2016, Samara, Russian Federation. Samara: Samara State Aerospace University Publ.; 2016. p.414‒418. (in Russ.) EDN:WMPXCP
10. Meeßen S.M., Thielsch M.T., Hertel G. Trust in Management Information Systems (MIS). Zeitschrift für Arbeits-und Organisationspsychologie A&O. 2019;64(1):6‒16. DOI:10.1026/0932-4089/a000306
11. Maqableh M., Hmoud H.Y., Jaradat M., Masadeh R. Integrating an information systems success model with perceived privacy, perceived security, and trust: the moderating role of Facebook addiction. Heliyon. 2021;7(9):1‒15. DOI:10.1016/j.heliyon.2021.e07899
12. Ettlie J.E., Tucci C., Gianiodis P.T. Trust, integrated information technology and new product success. European Journal of Innovation Management. 2017;20(30):406‒427. DOI:10.1108/EJIM-12-2015-0128
13. McKnight H., Carter M., Clay P. Trust in technology: Development of a set of constructs and measures. DIGIT 2009 Proceedings. 2009. URL: https://aisel.aisnet.org/digit2009/10 [Accessed 10.06.2024]
14. Ngo-Ye T.L., Nazareth D.L., Choi J.J. Trust in security as a service: a theoretical model. Issues in Information Systems. 2020;21(2);64‒74.
15. Park S. Multifaceted trust in tourism service robots. Annals of Tourism Research. 2020;81:102888. DOI:10.1016/j.annals.2020.102888
16. Ramos F.L., Ferreira J.B., Freitas A.S., Rodrigues J.W. The Effect of Trust in the Intention to Use m-banking. BBR. Brazilian Business Review. 2018;15(2):175‒191. DOI:10.15728/bbr.2018.15.2.5
17. Putra G.C., Astiti N.P.Y., Gunadi G.N.B. The Exploring of Trust that Influences Customer's Intention to Use FinnTech M-Banking Application on Regional Banks. International Journal of Economics and Business Administration. 2020;8(4):407‒421.
18. Itkes A.A. Combining logical access control models for complex distributed information systems. Problemy informatiki. 2010;3:85‒94. (in Russ.) EDN:NBRZPN
19. Glukhova L.V., Gubanova S.E. Some aspects of information security management of industrial complexes. Vestnik of Volzhsky University named after V.N. Tatishchev. 2015;3(34):135‒144. (in Russ.) EDN:VBWJDX
20. Gryzunov V.V. Conceptual Model for Adaptive Control of a Geographic Information System under Conditions of Destabilization. Automatic Control and Computer Sciences. 2021;55(8):1222–1227. DOI:10.3103/S0146411621080381
21. Pokrovskij I.A. To understand the concepts. IT Security. 2023;2:21‒22. (in Russ.).
22. Kalashnikov A.O., Bugajskij K.A., Birin D.S., Dereabin B.O., Tsependa S.O., Tabakov K.V. Application of the logical-probabilistic method in information security (part 1). Voprosy kiberbezopasnosti. 2023;4(56):23‒32. (in Russ.) DOI:10.21681/2311-3456-2023-4-23-32. EDN:GIHSBN
23. Zefferer T., Prunster B., Kollmann C., Corici A.A. A Security-Evaluation Framework for Mobile Cross-Border e-Government Solutions. Proceedings of the 24th Annual International Conference on Digital Government Research, 11‒14 July 2023, Gdansk, Poland. New York: Association for Computing Machinery; 2023. p.536‒543. DOI:10.1145/3598469.359852
24. Phiayura P., Teerakanok S. A Comprehensive Framework for Migrating to Zero Trust Architecture. IEEE Access. 2023;11:19487‒19511. DOI:10.1109/ACCESS.2023.3248622
25. Ahmadi S. Zero Trust Architecture in Cloud Networks: Application, Challenges and Future Opportunities. Journal of Engineering Research and Reports. 2024;26(2):215‒228. DOI:10.9734/jerr/2024/v26i21083
26. Khan M.J. Zero trust architecture: Redefining network security paradigms in the digital age. World Journal of Advanced Research and Reviews. 2023;19(3):105‒116. DOI:10.30574/wjarr.2023.19.3.1785
27. Gryzunov V.V. FIST geoinformation system model using fog computing in destabilization. Herald of Dagestan State Technical University. Technical Sciences. 2021;48(1):76‒89. (in Russ.) DOI:10.21822/2073-6185-2021-48-1-76-89. EDN:IDEYPX
28. Gryzunov V.V. Model of Purpose Aggressive Actions on the Information-Computing System. Proceedings of the 3rd International Conference on Human Factors in Complex Technical Systems and Environments, ERGO, 04‒07 July 2018, St. Petersburg, Russia. IEEE; 2018. p.119–121. DOI:10.1109/ERGO.2018.8443814
29. Gryzunov V.V., Bondarenko I.Yu. A Social Engineer in Terms of Control Theory. Proceedings of the 3rd International Conference on Human Factors in Complex Technical Systems and Environments, ERGO, 04‒07 July 2018, St. Petersburg, Russia. IEEE; 2018. p.202–204. DOI:10.1109/ERGO.2018.8443835
30. Gryzunov V., Gryzunova D. Problems of Providing Access to a Geographic Information System Processing Data of Different Degrees of Secrecy. In: Khanna K., Estrela V.V., Rodrigues J.J.P.C. (eds.) Cyber Security and Digital Forensics. Lecture Notes on Data Engineering and Communications Technologies, vol.73. Singapore: Springer; 2022. p.191–198. DOI:10.1007/978-981-16-3961-6_17
31. Anan'ev I.V., Serova E.G. Areas of effective application of IDEF0 notation for tasks of describing business processes. Vestnik of Saint Petersburg University. Management. 2008;2:161‒172. (in Russ.) EDN:JUBTXH
32. Kanev S.A. Determination of characteristics of a company's informational assets use efficiency. Creative Economy. 2010;8(44):42‒47. (in Russ.) EDN:MSVWFV
33. Manzhosov A.V., Bolodurina I.P., Saburov V.S., Dolgushev N.A Development of a special classification of information assets in the information security field. Bulletin of Perm University. Mathematics. Mechanics. Computer Science. 2022;4(59):54‒60. (in Russ.) DOI:10.17072/1993-0550-2022-4-54-60. EDN:ZHZWNB
Review
For citations:
Gryzunov V.V., Krjukov A.S., Shestakov A.V., Zikratov I.A. Ensuring Information Security of Information Systems to be Integrated Based on Trust. Proceedings of Telecommunication Universities. 2024;10(4):110-125. (In Russ.) https://doi.org/10.31854/1813-324X-2024-10-4-110-125. EDN: MZMYXF


































