Methodology for Reverse Engineering of Machine Code. Part 3. Dynamic Investigation and Documentation
https://doi.org/10.31854/1813-324X-2024-10-1-86-96
EDN: NZUJAZ
Abstract
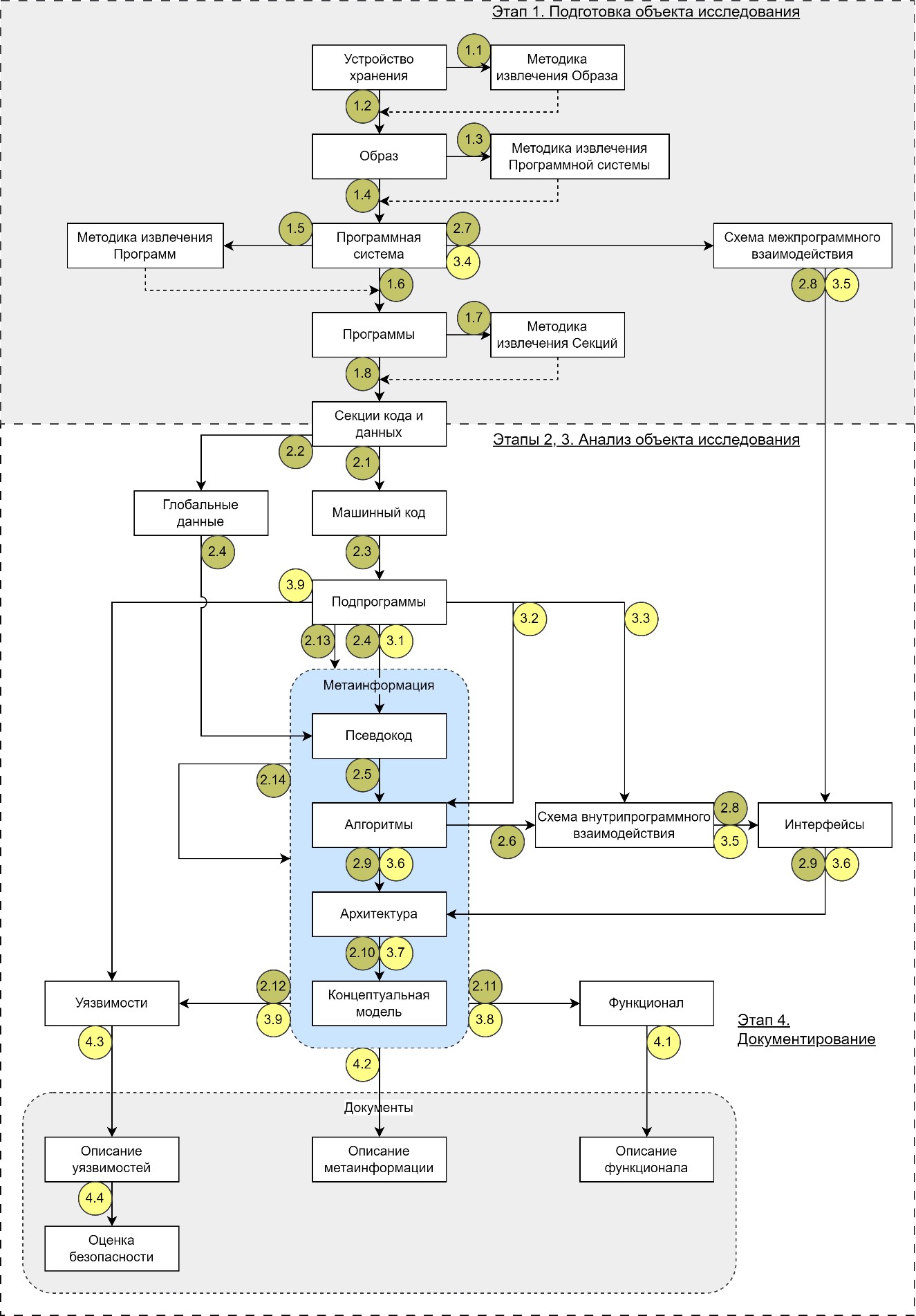
The results of creating a unified methodology for reverse engineering the machine code of devices are presented. This, the third and final part of the series of articles, is devoted to the dynamic examination of code in order to restore metainformation about it and additionally search for vulnerabilities, as well as the final documentation of the results. A review of scientific publications on the topic of existing methods and tools for dynamic analysis of machine code is carried out. A detailed description and formalization of the steps of the stage is given, as well as examples of their application in practice. A complete diagram of the proposed methodology is presented in graphical form, indicating the main and intermediate results obtained. All steps are summarized in a summary table, which also contains some of their characteristics. The shortcomings of the methodology and ways to eliminate them are discussed.
About the Author
K. IzrailovRussian Federation
References
1. Hendrix T.D., Cross J.H., Barowski L.A., Mathias K.S. Tool support for reverse engineering multi-lingual software. Pro-ceedings of the Fourth Working Conference on Reverse Engineering, 06−08 October 1997, Amsterdam, Netherlands. IEEE; 1997. p.136−143. DOI:10.1109/WCRE.1997.624584
2. Izrailov K. Methodology for Machine Code Reverse Engineering. Part 1. Preparation of the Research Object. Proceedings of the Telecommun. Univ. 2023;9(5):79–90. DOI:10.31854/1813-324X-2023-9-5-79-90. EDN:ZXLTBA
3. Izrailov K. Methodology for Machine Code Reverse Engineering. Part 2. Static Investigation. Proceedings of the Telecommun. Univ. 2023;9(6):68−82. DOI:10.31854/1813-324X-2023-9-6-68-82. EDN:SJSHCE
4. Kaushan V.V. Buffer overrun detection method in binary code. Proceedings of ISP RAS. 2016;28(5):135–144. DOI:10.15514/ISPRAS-2016-28(5)-8. EDN:VBDRBC
5. Guzik V.F., Zolotovskiy V.Ye., Savelev P.V. Performing mathematical operations in the symbolic computing system. Izvestiya SFedu. Engineering sciences. 2007;3(75):138−141. EDN:KTMRPB
6. Leoshkevich I.O. Obtaining architecture-independent semantics of executable code. Proceedings of IT Security (Russia). 2009;16(4):120−124. EDN:WTKHGF
7. Pereberina A.A., Kostyushko A.V. Development of tools for dynamic malware analysis. Proceedings of Moscow Institute of Physics and Technology. 2018;10(3):24−44. EDN:YZAJAD
8. Revnivykh A.V., Velizhanin A.S. Methods for Automated Formation of a Disassembled Listing Structure. Cybernetics and Programming. 2019;2:1−16. DOI:10.25136/2306-4196.2019.2.28272. EDN:TGCZKJ
9. Solovev M.A. Reconstructing the algorithm from a set of binary traces. PhD Thesis. Moscow: Ivannikov Institute for System Programming of the Russian Academy of Sciences Publ.; 2013. 123 p. EDN:SUSPIZ
10. Jimborean A., Herrmann M., Loechner V., Clauss P. VMAD: A virtual machine for advanced dynamic analysis of programs. Proceedings of International Symposium on Performance Analysis of Systems and Software, 10−12 April 2011, Austin, USA. IEEE; 2011. p.125−126. DOI:10.1109/ISPASS.2011.5762725
11. Cherchesov A.E. UEFI boot phases and how to control executable images. Voprosy zashchity informatsii. 2018;2(121):51–53. EDN:RSUTFZ
12. Safyallah H., Sartipi K. Dynamic Analysis of Software Systems using Execution Pattern Mining. Proceedings of the 14th IEEE International Conference on Program Comprehension, 14−16 June 2006, Athens, Greece. IEEE; 2006. p.84‒88. DOI:10.1109/ICPC.2006.19
13. Scherer K., Pfeffer T., Glesner S. I/O Interaction Analysis of Binary Code. Proceedings of the 28th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises, 12−14 June 2019, Napoli, Italy. IEEE; 2019. p.225−230. DOI:10.1109/WETICE.2019.00056
14. Lipayev V.V. Risks of design and production of mobile software products. Proceedings of ISP RAS. 2011;21:167−182. EDN:OKGXND
15. Izrailov K. Enetic Decompilation Concept of the Telecommunication Devices Machine Code. Proceedings of the Telecommun. Univ. 2021;7(4):10‒17. DOI:10.31854/1813-324X-2021-7-4-95-109. EDN:AIOFPM
16. Kotenko I., Izrailov K., Buinevich M. Static Analysis of Information Systems for IoT Cyber Security: A Survey of Machine Learning Approaches. Sensors. 2022;22(4):1335. DOI:10.3390/s22041335
Review
For citations:
Izrailov K. Methodology for Reverse Engineering of Machine Code. Part 3. Dynamic Investigation and Documentation. Proceedings of Telecommunication Universities. 2024;10(1):86-96. (In Russ.) https://doi.org/10.31854/1813-324X-2024-10-1-86-96. EDN: NZUJAZ


































